Mailbox messages with dangerous zip files.
These can appear in your mailbox disguised as a legitimate fax from a reputable company, in this case Xerox. . In fact, the link to Xerox is valid and will send you to their website. However, the same cannot be said about the attachment. Although innocent looking, it may contain dangerous zip files. A zip file can be used to get past email filters that will not allow an executable file to be delivered. This can properly be used to send a legitimate file to someone.
An Email with a Dangerous Zip File
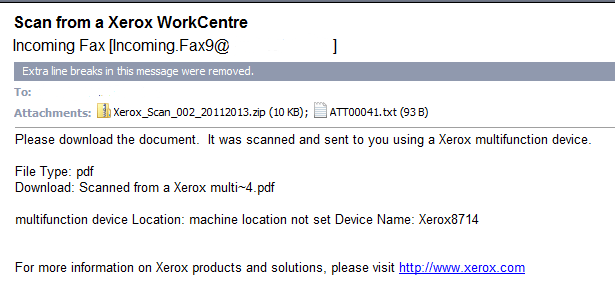
What are the clues that indicate that this email may contain dangerous zip files? 1. Look the address it is coming from. I do receive fax-to-email, but it contains my fax number and this one is obviously not from my fax to email forwarding agent. This one comes from an address I don’t recognize. 2.Who was it was sent to? The address used is different from what usually shows when I receive a fax. Compare that with faxes you normally receive as emails. All of mine are delivered to my mailbox with the same format. This one doesn’t fit the pattern. If you don’t receive fax to email, this tells you right away that it’s bogus.
DELETE IT RIGHT AWAY!
3. It says that the file type is pdf. This is one of the most common file types used in email attachments. There would be no reason to put it in a zip file. If you’re still not sure, what can you do? The first thing is DON’T OPEN IT! Check it first.
Scan the file!
You can check it by copying the zip file to your desktop and then checking it with your anti-virus. Most of these will have a menu item to check an individual file. for example, Vipre has a right-click that allows you to “Scan with Vipre”. See if your anti-virus has the same thing. It should scan the file and then give you a report as to whether it is safe. In this case it was quarantined and then removed. If it comes up as a virus, go back to the email and delete it right away. Just to be safe, you can go to the deleted items folder and remove it permanently. These are designed to get information from you that you would not normally forward to a stranger. Here is the report generated by Vipre Internet Security after scanning the Zip file. Risk name: Trojan.Win32.Generic!SB.0 Source: Scanner Risk level: High Risk category: Trojan Description: Trojan is a general term for malicious software that is installed under false or deceptive pretenses or is installed without the user’s full knowledge and consent. Most Trojans exhibit some form of malicious, hostile, or harmful functionality or behavior. Advice: This is a high risk and should be removed immediately as it may compromise your privacy and security, make dangerous changes to your computer’s settings without your knowledge and consent, or severely degrade your computer’s performance and stability.
Password-stealing Trojan Horse
A little research revealed that this dangerous zip file was a password stealing program. It would be able to log your keystrokes, so that if you entered a username and password for your online banking, for example, it would send that data back to people who could use it to steal your identity and/or your funds, or use your credit cards and other sensitive items. Here is another description from ThreatTrack Security Trojan.Win32.Generic!SB.0 is the generic detection for password-stealing Trojan horse programs that install key loggers which record keystrokes and send the data to the malicious operators who distributed the malware. If you see a zip file in your mailbox DO NOT OPEN IT! until you know it is safe. If this type of file is contained in an email from someone you know, don’t open it. Send an email or call the person who supposedly sent it and make sure it was from them and intended for you. Don’t be fooled by important sounding subject matter, perhaps to do with your payroll or tax matters. They try to make these things important or urgent so that you will open them. Be cautious. Safe computing to all!
Footnote: About the Trojan Horse
The term comes from the a Greek story of the Trojan War, in which the Greeks give a giant wooden horse to their foes, the Trojans, ostensibly as a peace offering. But after the Trojans drag the horse inside their city walls, Greek soldiers sneak out of the horse’s hollow belly and open the city gates, allowing their compatriots to pour in and capture Troy – http://www.webopedia.com/TERM/T/Trojan_horse.html
Still seeking to gain entrance into Troy, clever Odysseus (some say with the aid of Athena) ordered a large wooden horse to be built. Its insides were to be hollow so that soldiers could hide within it. Once the statue had been built by the artist Epeius, a number of the Greek warriors, along with Odysseus, climbed inside. The rest of the Greek fleet sailed away, so as to deceive the Trojans. One man, Sinon, was left behind. When the Trojans came to marvel at the huge creation, Sinon pretended to be angry with the Greeks, stating that they had deserted him. He assured the Trojans that the wooden horse was safe and would bring luck to the Trojans. Only two people, Laocoon and Cassandra, spoke out against the horse, but they were ignored. The Trojans celebrated what they thought was their victory, and dragged the wooden horse into Troy. That night, after most of Troy was asleep or in a drunken stupor, Sinon let the Greek warriors out from the horse, and they slaughtered the Trojans. Today the Trojan Horse refers to any program that like the ancient Greek gift of a horse, appears to be innocent and even welcome, but in reality is designed to create havoc and damage.